Research
Security Analysis of Commercial Cellular Devices and Networks
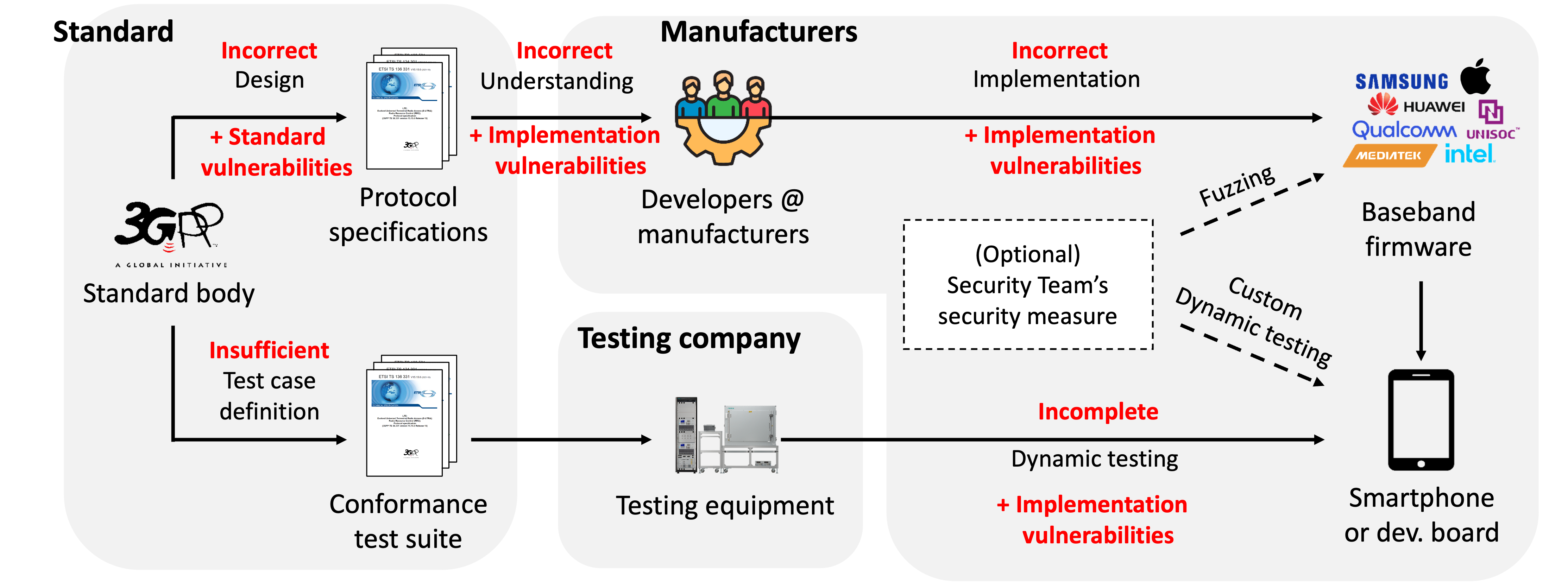
Modern cellular systems—from legacy 2G networks to today’s 5G Standalone architecture—rely on complex protocol layers such as NAS, RRC, and SIP (VoNR). Although these protocols are standardized, both their design and implementation often contain subtle security flaws.
Our research focuses on identifying vulnerabilities in real-world devices and infrastructure through over-the-air testing, protocol fuzzing, and specification-driven analysis. We analyze how deviations from standards, ambiguous procedures, or under-specified behaviors can lead to security issues. We also study the attack surfaces introduced by open and disaggregated architectures like ORAN.
Our goal is to uncover both implementation-level bugs and standard-level design weaknesses that can impact the confidentiality, integrity, or availability of cellular services.
Focus areas:
- NAS/RRC/VoNR protocol fuzzing using OTA interfaces
- State-machine inconsistency and authentication bypass
- Exploit scenarios involving malformed signaling, rogue reconfiguration, and spec violations
- Security analysis of ORAN interfaces (e.g., E2, A1, O1) and components (DU/CU)
Security in Satellite and Non-Terrestrial Networks (NTN)
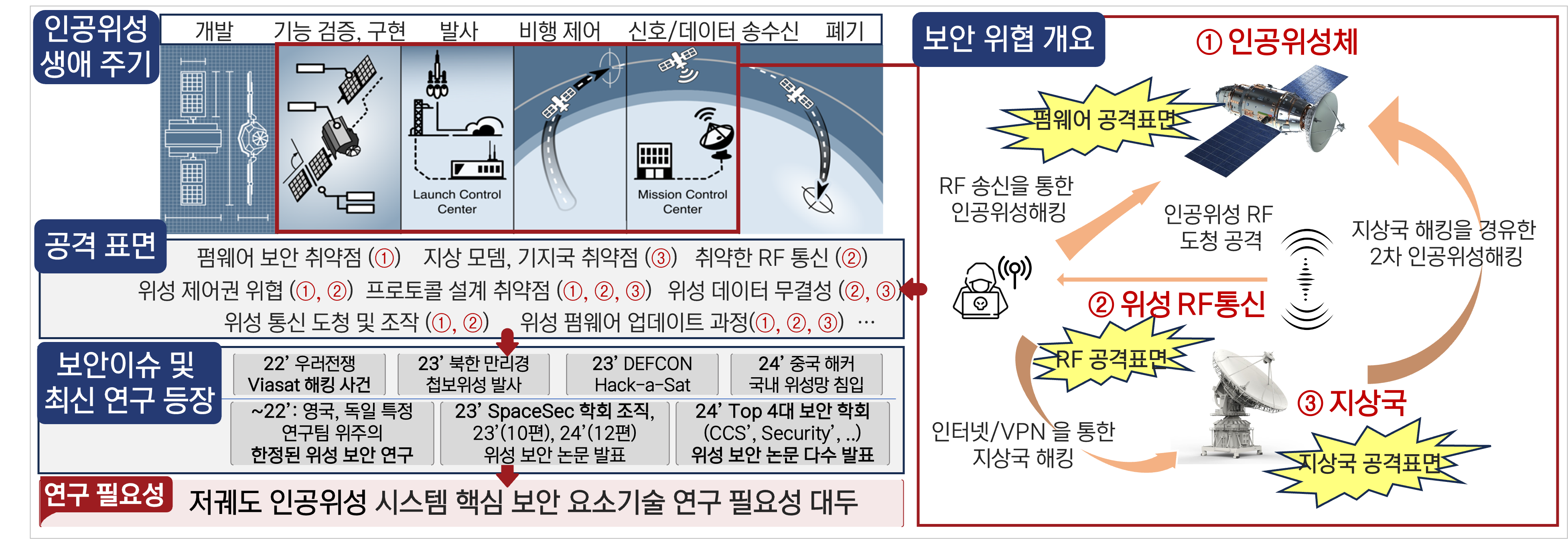
As the 3GPP standard extends cellular connectivity to non-terrestrial networks (NTNs), dedicated satellite systems for 5G-NTN are being actively developed and standardized. Also, low Earth orbit (LEO) satellites—such as commercial communication satellites and CubeSats for IoT backhaul or remote coverage—are being widely deployed, expanding the mobile attack surface beyond terrestrial infrastructure.
We analyze how key 5G NTN procedures, such as access and mobility management, behave under satellite constraints, and how they can be exploited. Our research also investigates practical threats including signal spoofing, unauthorized uplink transmission by rogue terminals, and the risks of over-the-air manipulation in satellite-based networks.
Focus areas:
- 5G NTN security testing, evaluation
- Over-the-air spoofing and unauthorized uplink transmission
- CubeSat and LEO satellite-specific security risks
- Signal manipulation and eavesdropping threats in satellite environments
Detection and Mitigation of Fake Base Stations and Malicious UEs
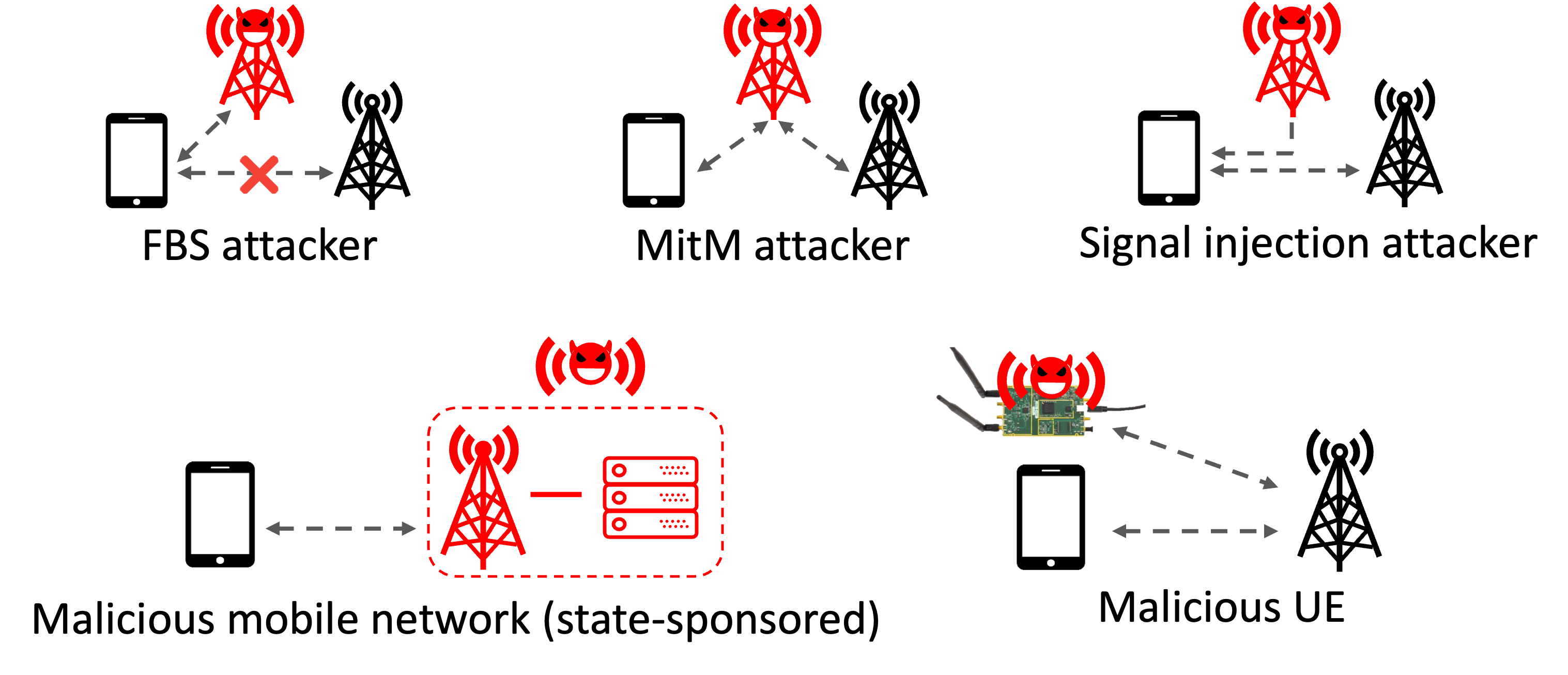
Fake base stations (FBS), often used in IMSI-catching or downgrade attacks, pose a persistent threat to mobile network users. Beyond passive eavesdropping, active rogue nodes and malicious devices can exploit protocol weaknesses to deny service, intercept messages, or inject malicious signaling into the network.
Our work builds detection and defense mechanisms against such rogue entities. We develop methods to monitor abnormal protocol behaviors, detect signaling anomalies, and even trace physical-layer signatures of malicious transmitters. We also explore ways to defeat unauthorized service access attempts.
Field experiments and testbed deployments are an essential part of this work, using SDR platforms and controlled attack emulation in live networks.
Focus areas:
- Detection of fake base stations
- Defense system for fake base station and malicious UEs
- Behavior analysis of malicious UEs exploiting spec corner cases
- Physical-layer and signaling-layer anomaly detection
Other Research Directions
In addition to our core research areas, we also explore several emerging and interdisciplinary topics in wireless and systems security. These projects are driven by curiosity, collaboration, and the goal of expanding our understanding of how modern systems behave in adversarial environments.
These include:
- AI-guided protocol testing and vulnerability discovery in cellular systems
- LLM-assisted analysis of cellular standards, including automated extraction of protocol procedures and test input generation
- Security analysis of low-power wireless systems
- Sensor-based attacks and signal-level interference
- Early-stage investigations into physical-layer manipulation, side channels, and wireless privacy threats